Cloud Computing Patterns, Mechanisms > Mechanisms > I - P > Public Key Infrastructure
Public Key Infrastructure
A common approach for managing the issuance of asymmetric keys is based on the public key infrastructure (PKI) mechanism, which exists as a system of protocols, data formats, rules, and practices that enable large-scale systems to securely use public key cryptography. This system is used to associate public keys with their corresponding key owners (known as public key identification) while enabling the verification of key validity. PKIs rely on the use of digital certificates, which are digitally signed data structures that bind public keys to certificate owner identities, as well as to related information, such as validity periods. Digital certificates are usually digitally signed by a third-party certificate authority (CA).
Other methods of generating digital signatures can be employed, even though the majority of digital certificates are issued by only a handful of trusted CAs. Larger organizations, such as Microsoft, can act as their own CA and issue certificates to their clients and the public, since even individual users can generate certificates as long as they have the appropriate software tools.
Building up an acceptable level of trust for a CA is time-intensive but necessary. Rigorous security measures, substantial infrastructure investments, and stringent operational processes all contribute to establishing the credibility of a CA. The higher the level of trust and reliability, the more esteemed and reputable the certificates are. The PKI is a dependable method for implementing asymmetric encryption, managing cloud consumer and cloud provider identity information, and helping to defend against malicious intermediaries and ineffective authorization.
Trustworthiness is of critical importance as it is the security assurance level of the PKI that is mandated by many of the industry compliance standards. The PKI issues certificates that can be trusted to the indicated level of assurance that is documented in the PKI certificate policy statement and security practice statement. Auditors are used to confirm that the PKI is operating according to the associated certificate practice statement.
The components of a PKI include a CA that issues the certificates, a registration authority (RA) to approve issuance of the certificates, a public directory containing the issued certificates, and the certificate revocation list (CRL).
The following steps are shown in Figure 1:
- The consumer (end entity) requests a certificate, creating a private key.
- The RA vets the consumer, and if appropriate, approves issuance and notifies the CA.
- The CA issues the certificate containing the corresponding public key.
The private key is activated by a PIN and kept confidential by the consumer. For encryption and in order to use the certificate for authentication, the consumer must prove possession of the private key. The issuing CA signs the certificate with the CA signing certificate, which is used as part of the process in validating the consumer’s certificate.
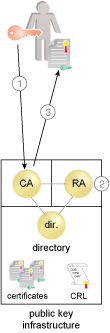
Figure 1 – A public key infrastructure with a certificate authority, registration authority, and a directory to hold certificates and CRLs.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


