Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Cloud Traffic Hijacking Protection
Cloud Traffic Hijacking Protection (Cope, Erl)
How can cloud communication be protected from traffic hijacking?

Problem
Attackers can often locate Internet service providers (ISPs) whose internal or ISP-to-ISP Border Gateway Protocol (BGP) session is susceptible to a man-in-the-middle attack. Once located, an attacker can potentially advertise any prefix they want, causing some or all traffic to be diverted from the real source towards the attacker.
Solution
A series of mechanisms are established to ensure mutually authenticated and encrypted communications data channels where possible, encryption and integrity protection of data in transit between the cloud consumer and cloud provider, as well as the monitoring and alerting of traffic anomalies.
Application
Cloud traffic hijacking attacks can be mitigated using either a third party and/or on-premise traffic monitoring system in conjunction with validated encryption and digital signatures or authentication codes for the data in transit.
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
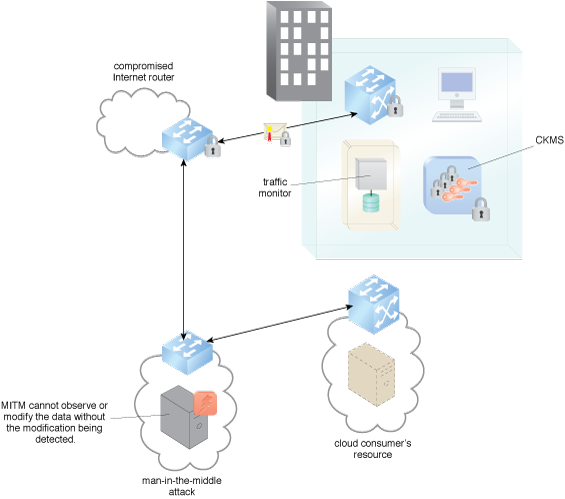
Various traffic hijacking mitigations are executed.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


