Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Geotagging
Geotagging (Cope, Erl)
How can the geographic location of cloud-based data and workloads be automatically communicated?

Problem
Control of data, workload locality and data sovereignty are requirements for federal and industrial compliance and regulatory issues. Without knowledge of where a cloud consumer’s workload is executed, it may not be possible to meet industrial compliance and regulatory requirements for data sovereignty.
Solution
When trusted resource pools are generated, the geolocation is supplied as part of the compliance and regulatory assurance attributes.
Application
Assets are geotagged using TPMs and are added to trusted resource pools that contain the same security assurance levels and geolocation regions.
Mechanisms
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
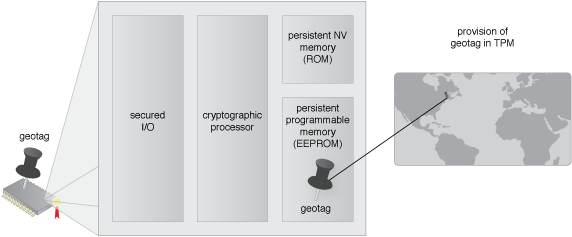
The geolocation is configured in the TPM.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


