Cloud Computing Patterns, Mechanisms > Mechanisms > T - Z > Virtual Private Network
Virtual Private Network

The virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide consumers with secure connections to their organization’s network. The VPN ensures privacy through security procedures and tunneling protocols, including the Layer Two Tunneling Protocol (L2TP). Data is encrypted at the sending end for transmission and decrypted at the receiving end.
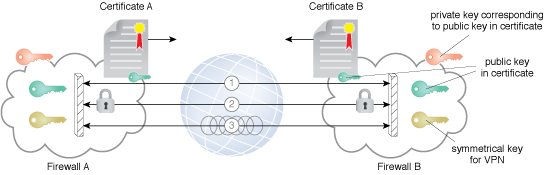
Figure 1 – A virtual private network established between two clouds.
Figure 1 shows two firewalls establishing a VPN between two clouds. They first exchange each other’s certificates and use asymmetric encryption to securely exchange keying material to establish efficient symmetric key encryption. IPsec is a framework of open standards for private communications over public networks. It is a network layer security control that is used to create the VPN.
There are three VPN architectures:
- The gateway-to-gateway architecture protects communications between two networks, such as an organization’s on-premise network and the organizations cloud resources.
- The host-to-gateway architecture protects communications between one or more individual hosts and a network. The host-to-gateway model is used to allow hosts on unsecured networks, such as traveling employees and telecommuters, to gain access to internal organizational services.
- The host-to-host architecture protects communication between two specific computers. It is used when a small number of users need to use or administer a remote system that requires the use of inherently insecure communications protocols.
Related Patterns:
- Automatically Defined Perimeter
- Cloud Authentication Gateway
- Secure External Cloud Connection
- Secure On-Premise Internet Access
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


