Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Secure External Cloud Connection
Secure External Cloud Connection (Cope, Erl, Kristan)
How can a cloud network establish a secure connection with on-premise IT resources?

Problem
Solutions and service compositions can be required to execute partially in the cloud and partially on-premise due to scaling requirements, compliance regulations or organizational policy, creating the need for secure connectivity.
Solution
A virtual private network (VPN) is used to establish an encrypted connection between the cloud service provider and the cloud consumer.
Application
A VPN is established between the cloud consumer gateway (CCG) and the cloud provider’s virtual private gateway (VPG) using the Border Gateway Protocol (BGP).
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)

A secure connection is established between the cloud consumer network and virtual private cloud.
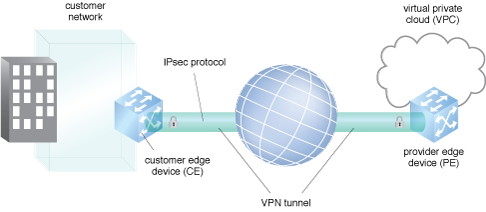
A customer network securely connected to a VPC.
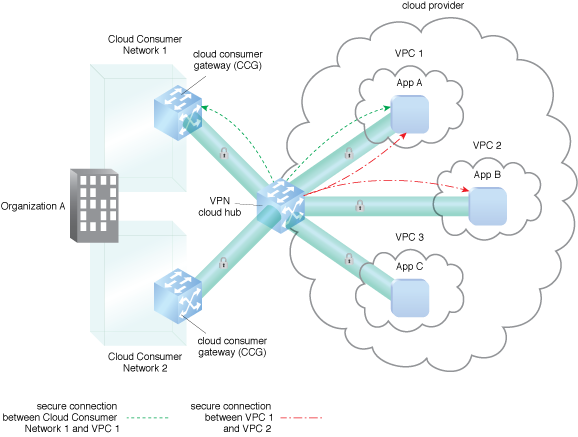
VPN connections are established via the use of a cloud hub.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


