Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Automatically Defined Perimeter
Automatically Defined Perimeter (Cope, Erl)
How can a perimeter be protected that is dynamic and extends from on-premise to multi-vendor cloud resources?

Problem
In cloud architecture, IT boundaries are dynamic and can scale into multiple clouds from on-premise resources, which creates challenges when establishing and securing perimeters.
Solution
A system is established that provides protected communications between consumers and providers whereby each provider either accepts or rejects communications based on privileges securely granted automatically by a perimeter controller.
Application
Cloud consumers authenticate to an automatically defined perimeter (ADP) controller which, if they are authorized, notifies the appropriate cloud provider services to respond to the authenticated consumer’s requests. Otherwise, protected providers do not respond to any communications.
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
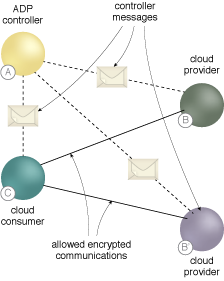
ADP cloud services can either be: cloud consumers requesting a single service, multiple services, or a service orchestration (A), cloud providers that initially only respond only to the ADP controller and then only to cloud consumers that have been authorized by the ADP controller (B), access managed by requests to ADP controllers which rely on the organization’s IAM (C).
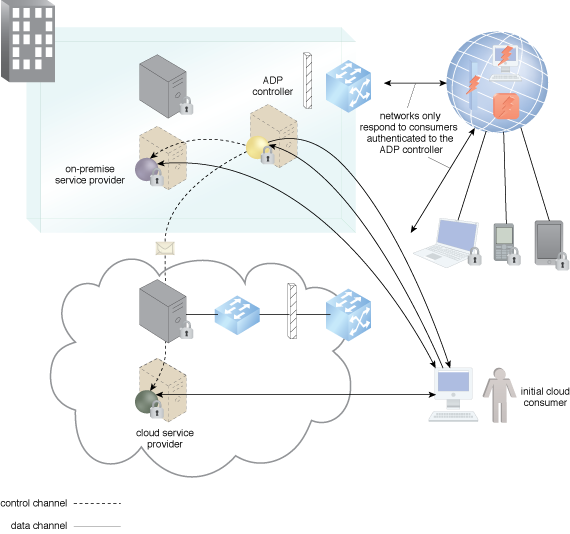
The participating cloud resources authenticate to the ADP and register with it when they are initially brought online.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


