Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Trusted Cloud Resource Pools
Trusted Cloud Resource Pools (Cope, Erl)
How can cloud-based resource pools be secured and become trusted?

Problem
Cloud platform pool security needs to be achieved to meet cloud consumer compliance and regulatory security requirements. Verification of the platform assurance level is critical for regulated industries.
Solution
Trusted resource pools made up of trusted geotagged computers are made available by the cloud provider, and can be verified by the consumer through direct monitoring or evidence through auditing.
Application
Achieving security through the use of trusted platform modules (TPMs), validating digitally signed code, geotagging, and remote monitoring of the platform security status, cloud consumers can verify that they are using compute platforms that meet their security assurance requirements.
Mechanisms
Attestation Service, Certificate, Cloud Workload Scheduler, Digital Signature, Geotag, Platform Trust Policy, Trusted Platform Module
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
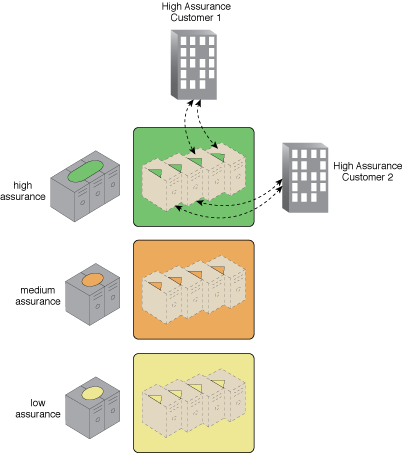
Resources pooled by security assurance level.
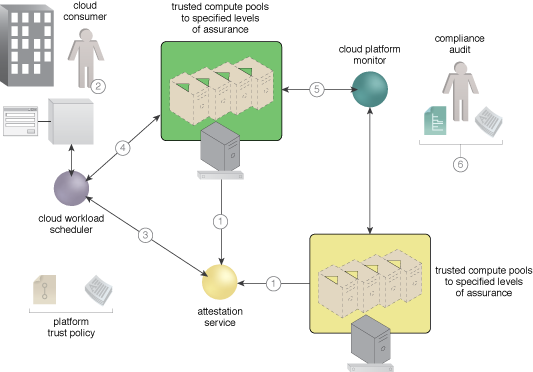
A sequence for creating and using trusted resource pools.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


