Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Detecting and Mitigating User-Installed VMs
Detecting and Mitigating User-Installed VMs (Cope, Erl)
How can user-installed VMs from non-authorized templates be detected and secured?

Problem
Virtual machines that are installed from cloud consumer templates need to be discovered and secured from any known vulnerabilities. An IaaS consumer has the ability to install VMs that have not been vetted for security by the cloud provider.
Solution
A system that includes an internal usage policy can be established, providing network and endpoint security that is VM-aware in order to locate and identify virtual machines and report and secure them.
Application
Using host-based security, including host-based VM discovery software, emergent VMs can be discovered and reported for further processing.
Mechanisms
Hardened Virtual Server Image, Hardware-Based VM Discovery System, Host Based Security System, Hypervisor, Virtual Infrastructure Manager
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
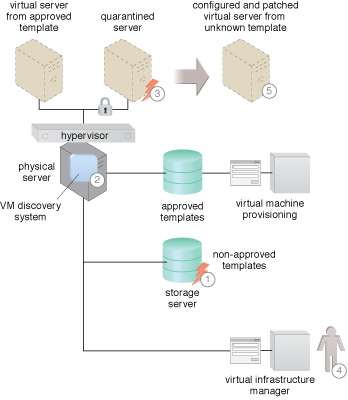
A non-approved VM is installed on a hardware server (1). The VM discovery system discovers a rogue VM (2). The VM discovery system quarantines the VM (3). The discovery system alerts an administrator (4). The administrator takes steps to configure and patch the VM to meet security requirements for use. Alternately, they could make the determination that an approved template can meet the requirements of the consumer and replace the vulnerable template (5).
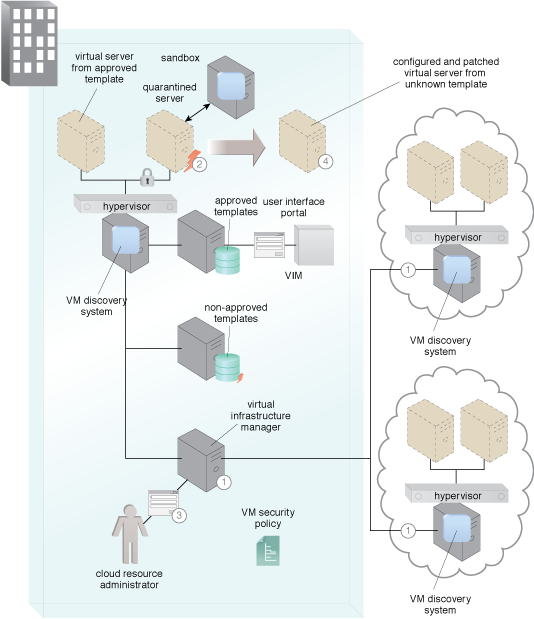
A master VM discovery system monitor communicates with each host’s VM Discovery System. It sets the security policy describing what security profile the VMs should meet (1). It monitors the number and security state of each VM according to policy and part of internal usage policy, alerting if a rogue VM is discovered. It takes both immediate automatic mitigation steps as well as alerting administrators. Mitigation steps can include moving image to a sandbox area for provisioning and eliminating any networking possibilities as a quarantine measure. It controls multiple platforms both on-premise and in the cloud (2). The monitoring system alerts the administrator of anonymous situations and actions taken (3). The monitoring system mitigation steps establish a properly provisioned VM ready for addition to the network and enterprise (4).
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


