Cloud Computing Patterns, Mechanisms > Mechanisms > D - H > Hardware Security Module
Hardware Security Module

The hardware security module (HSM) is a dedicated hardware cryptographic processor that is designed for the protection of the encryption key lifecycle. HSMs provide the capability to securely manage, process, and store encryption keys inside a hardened tamper-resistant device that is also resistant to bus probing. High assurance HSMs normally have features that provide tamper evidence, such as logging and alerting, and tamper resistance, such as deleting keys upon tamper detection. HSMs are mission critical as they manage the cryptography that is foundational for security, and are typically clustered for high availability.
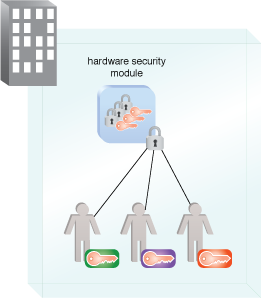
Figure 1 – An example of an HSM with split key administration.
Figure 1 shows a hardened on-premise HSM. It can be a separate network-attached device with keys for multiple resources, or attached directly to the resource for which it is protecting keys.
Typically, HSMs are managed by administrators filling trusted roles using separation of duties (SOD) so that they require multiple administrators to accomplish management tasks. To protect the integrity of each role, the administrators have their own safes or security containers that contain materials supporting protection of keys. They have split keys protecting HSMs that, when combined, can enable management functions. Trusted role operations include installation, configuration and maintenance of the HSM, access to restricted keys, and the ability to grant physical and/or logical access to the HSM equipment.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is also covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


