SOA Patterns > Service Interaction Security Patterns > Data Confidentiality
Data Confidentiality (Hogg, Smith, Chong, Hollander, Kozaczynski, Brader, Delgado, Taylor, Wall, Slater, Lmran, Cibraro, Cunningham)
How can redundant utility logic be avoided across domain service inventories?

Problem
Within service compositions, data is often required to pass through one or more intermediaries. Point-to-point security protocols, such as those frequently used at the transport-layer, may allow messages containing sensitive information to be intercepted and viewed by such intermediaries.
Solution
The message contents are encrypted independently from the transport, ensuring that only intended recipients can access the protected data.
Application
A symmetric or asymmetric encryption and decryption algorithm, such as those specified in the XML-Encryption standard, is applied at the message level.
Impacts
This pattern may add runtime performance overhead associated with the required encryption and decryption of message data. The management of keys can further add to governance burden.
Principles
Architecture
Inventory, Composition, Service
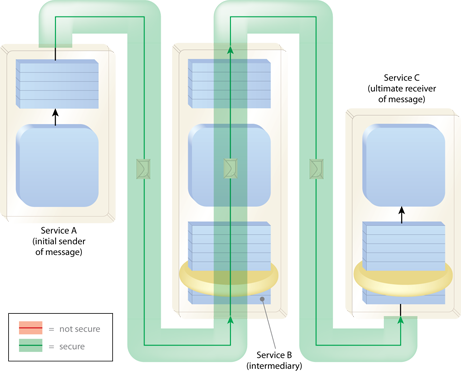
Data Confidentiality protects the message while in transit between services and while in the possession of unauthorized intermediaries.
Related Patterns in This Catalog
Brokered Authentication, Data Origin Authentication, Direct Authentication, Messaging Metadata, Service Agent, Service Messaging, State Messaging
Related Service-Oriented Computing Goals
This pattern is covered in SOACP Module 18: Fundamental Security for Services, Microservices & SOA.
For more information regarding the SOA Certified Pofessional (SOACP) curriculum,
visit www.arcitura.com/soa.
This page contains excerpts from:
SOA Design Patterns by Thomas Erl
(ISBN: 0136135161, Hardcover, Full-Color, 400+ Illustrations, 865 pages)
For more information about this book, visit www.arcitura.com/books.

