Blockchain Patterns, Mechanisms, Models, Metrics > Security and Privacy Patterns > Federated Chain
Federated Chain (Erl, Naserpour)
How can different organizations that do not trust each other participate in the same blockchain network without sharing security domains?
Problem
For multiple organizations to participate in a permissioned community blockchain network, they may be required to share their security boundaries and confidential login credentials with non-trusted parties.
Solution
A third-party authentication service or a designated, trusted organization is used to authenticate partners without requiring them to otherwise share their security domain or expose their login credentials.
Application
The identity federator mechanism is utilized by a neutral third-party service provider or by a trusted blockchain participant (such as a government agency) to assume the responsibility of authenticating all participating partners without requiring them to share security domains.
Mechanisms
Identity Federator, Identity Verifier
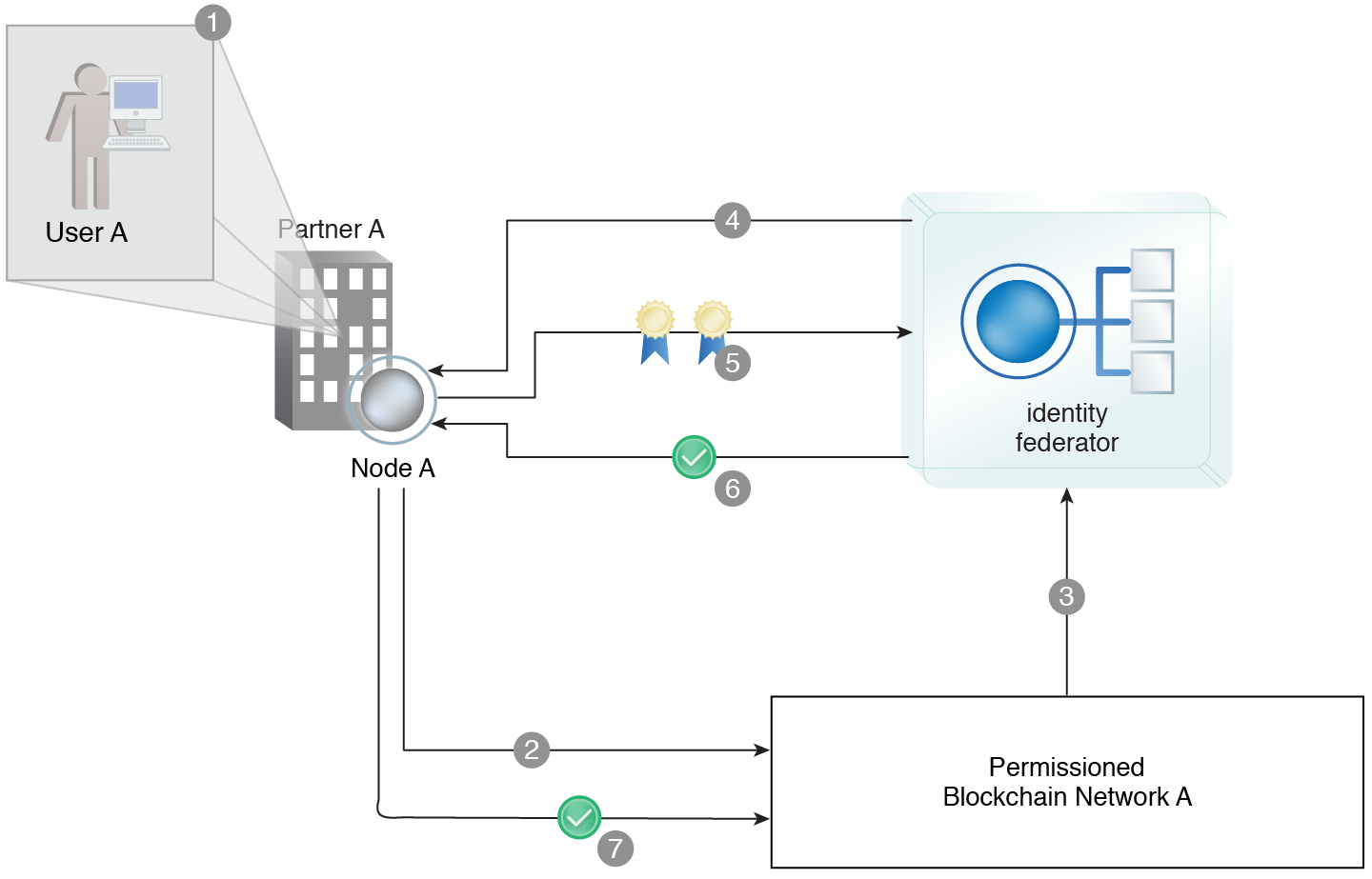
User A from Partner A logs into its network via the local IAM (1). User A attempts to access Permissioned Blockchain Network A (2). The blockchain application forwards User A’s request to a third party identity federation service (3). The identity federator mechanism asks Node A to provide its user and workstation certificates (4). Node A provides the requested certificates (5). The identity federator successfully authenticates Node A and issues an identity token to Node A (6). Node A successfully accesses Permissioned Blockchain Network A using the identity token and User A is able to act as a blockchain application participant (7).
This pattern is covered in Blockchain Module 2: Blockchain Technology & Architecture.
For more information regarding the Blockchain Architect curriculum, visit www.arcitura.com/blockchain.
