Cloud Computing Patterns, Mechanisms > Monitoring, Provisioning and Administration Patterns > Resource Management
Resource Management (Erl, Naserpour)
How can a cloud consumer safely manage an IT resource without impacting neighboring IT resources?

Problem
When cloud consumers access and manage deployed IT resources that coexist with other IT resources as part of a live production environment, management changes to an IT resource may inadvertently negatively impact others.
Solution
A set of tools and backend controls are provided by the cloud provider to protect the management activity of one cloud consumer from others.
Application
Cloud consumers are given limited access levels and management options and their management activity is further confined to their respective logical network perimeters.
Mechanisms
Audit Monitor, Cloud Usage Monitor, Logical Network Perimeter, Remote Administration System, Resource Management System
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
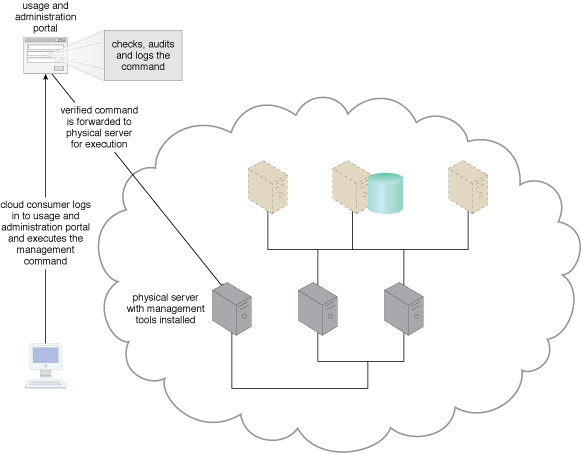
Cross-IT resource management tools and logic are used to check (and optionally audit and log) commands before allowing them to be executed.
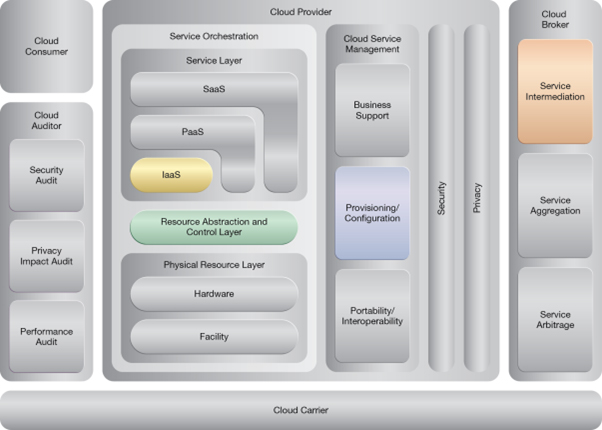
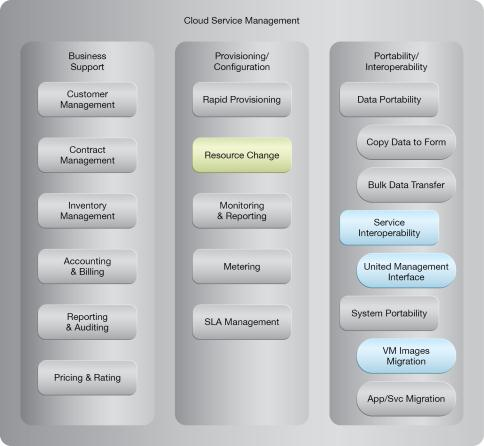
NIST Reference Architecture Mapping
This pattern relates to the highlighted parts of the NIST reference architecture, as follows:
This pattern is covered in CCP Module 4: Fundamental Cloud Architecture.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
