Cloud Computing Patterns, Mechanisms > Mechanisms > D - H > Honeypot
Honeypot

Honeypots are used to trap attackers into thinking that they have penetrated a network, allowing time for defenders to analyze their threat parameters and generate appropriate threat indicators to block an impending attack. Honeypots are decoy systems providing hosts that have no authorized users other than the honeypot administrators, as they serve no business function.
Honeypots collect data on threats and activity directed at them that is considered suspicious. Honeypots can be set up inside, outside, in the DMZ, or in all three locations. They are most often deployed inside of a firewall for control purposes. Honeypots are variants of standard intrusion detection and prevention systems (IDPSs) but with a greater focus on information gathering and deception.
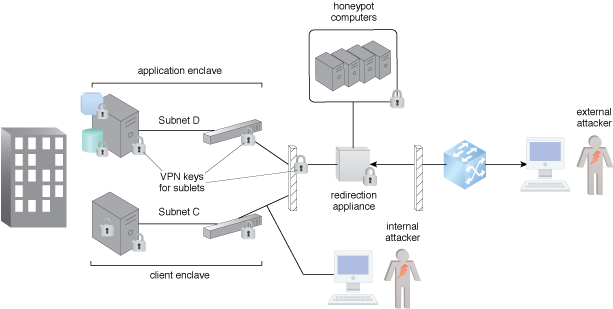
Figure 1 – An example of a honeypot architecture.
When an attacker scans a network, they are redirected to the honeypot system via a VPN, as shown in Figure 1. The honeypot computers mimic operational devices but threat intelligence is gathered by observing the attacker’s actions, detecting the earliest signs of widespread incidents so that the organization can collect better data on these threats.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is also covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


