Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Hypervisor Protection
Hypervisor Protection (Cope, Erl)
How can a hypervisor be secured and monitored?
Problem
The hypervisor is vulnerable to threats from multiple vectors and, if compromised, could attack any other component that is shared by the same hypervisor.
Solution
A system is established whereby mitigations are implemented from the silicon up the stack to protect against hypervisor attack vectors.
Application
A hardened hypervisor is installed and verified using a trusted platform and mitigations are added to protect against vulnerabilities.
Mechanisms
Digital Signature, Hardened Virtual Server Image, Host Based Security System, Trusted Platform Module
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
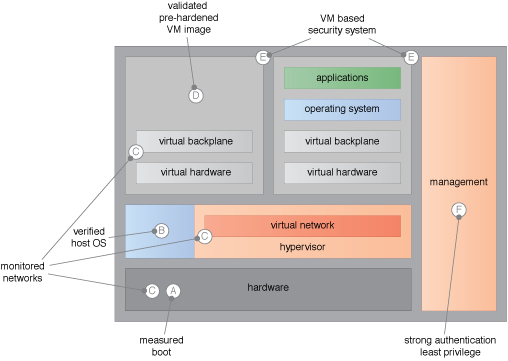
Examples of hypervisor threat mitigations.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


