Cloud Computing Patterns, Mechanisms > Mechanisms > D - H > Digital Signature
Digital Signature

The digital signature mechanism is a means of providing data authenticity and integrity through authentication and non-repudiation. A message is assigned a digital signature prior to transmission, which is then rendered invalid if the message experiences any subsequent, unauthorized modifications. A digital signature provides evidence that the message received is the same as the one created by its rightful sender.
Both hashing and asymmetrical encryption are involved in the creation of a digital signature, which essentially exists as a message digest that was encrypted by a private key and appended to the original message. The recipient verifies the signature validity by using the corresponding public key to decrypt the digital signature’s encrypted hash, which produces the message digest. The hashing mechanism is applied to the original message to produce the message digest. Identical results from the two different processes indicate that the message maintained its integrity.
The digital signature mechanism helps mitigate the malicious intermediary, insufficient authorization, and overlapping trust boundary’s security threats (Figure 1).
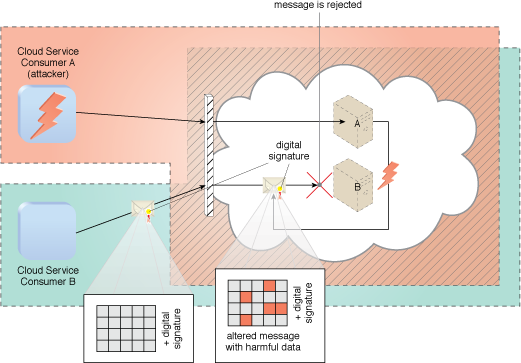
Figure 1 – Cloud Service Consumer B sends a message that was digitally signed but was altered by trusted attacked Cloud Service Consumer A. Virtual Server B is configured to verify digital signatures before processing incoming messages even if they are within its trust boundary. The message is revealed as illegitimate due to its invalid digital signature, and is therefore rejected by Virtual Server B
Related Patterns:
- Cloud Traffic Hijacking Protection
- Hypervisor Protection
- In-Transit Cloud Data Encryption
- Secure Connection for Scaled VMs
- Trust Attestation Service
- Trusted Cloud Resource Pools
- Trusted Platform BIOS
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is also covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


