Big Data Patterns, Mechanisms > Data Transfer and Transformation Patterns > Integrated Access
Integrated Access (Buhler, Erl, Khattak)
How can users seamlessly access enterprise IT systems and a Big Data platform’s resources without having to authenticate twice?

Problem
Solution
Application
Mechanisms
A security engine mechanism is used to provide the necessary integration with the enterprise IAM. The security engine is configured to integrate with the required IAM. Internally, the security engine maps the user identities provided by the IAM, generally in the form of a token, to Big Data platform-specific identities. These identities are then used to access different resources. It is important to choose a security engine implementation that provides integration with multiple IAMs and security protocols to ensure the fulfillment of current and future security integration requirements. This pattern is normally applied together with the Centralized Access Management pattern.
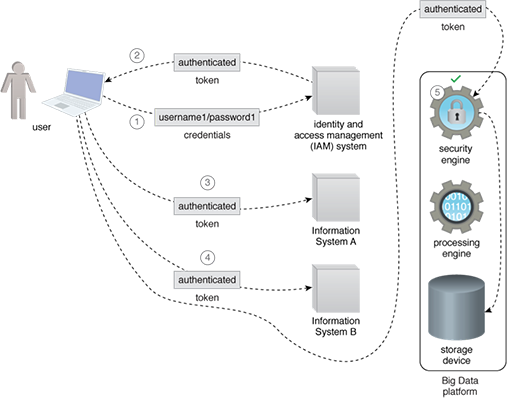
A system is set up that integrates the Big Data platform’s security module with the enterprise identity and access management system to create an SSO system. This provides a seamless experience to the user, as the user is not required to re-authenticate. The responsibility of performing the authentication is delegated to the IAM, and the Big Data platform security module trusts the IAM.
- A user, who needs to access two enterprise information systems, forwards their credentials to an identity and access management (IAM) system.
- After successful authentication, a token is sent by the IAM to the user as a proof that they have authenticated themselves successfully.
- To access Information System A, the user simply provides the token to Information System A, which grants access without asking the user to present their credentials again.
- To access Information System B, the user simply provides the token to Information System B, which grants access without asking the user to present their credentials again.
- When the user tries to access the Big Data platform’s storage device with the same token, the token is inspected by the security engine, and access is granted without asking the user to present their credentials again.
This pattern is covered in BDSCP Module 11: Advanced Big Data Architecture.
For more information regarding the Big Data Science Certified Professional (BDSCP) curriculum,
visit www.arcitura.com/bdscp.
The official textbook for the BDSCP curriculum is:
Big Data Fundamentals: Concepts, Drivers & Techniques
by Paul Buhler, PhD, Thomas Erl, Wajid Khattak
(ISBN: 9780134291079, Paperback, 218 pages)
Please note that this textbook covers fundamental topics only and does not cover design patterns.
For more information about this book, visit www.arcitura.com/books.

