Cloud Computing Patterns, Mechanisms > Mechanisms > I - P > Network Forensic Monitor
Network Forensic Monitor

Network forensics identifies the source of intermittent performance issues and supports investigations to identify the source of data leaks, policy violations, or security breaches. The network forensics monitor captures, records, and analyzes network events in order to discover the source of security attacks or other problem incidents. Computer forensics involve the preservation, identification, extraction, documentation, and interpretation of computer media for evidentiary and/or root cause analysis. Network forensics monitors aid in acquiring and analyzing evidence.
The network forensics monitor can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports, etc. without putting any traffic on the network. It can also parse packet capture (PCAP) files for offline analysis and regenerate or reassemble transmitted files and certificates from PCAP files.
Network forensics monitors are queued by threat intelligence systems to discover possible successful attacks. Figure 1 illustrates a network forensics monitor incorporating a threat intelligence system to queue for possible threats. This allows it to search for particular possible intrusions.
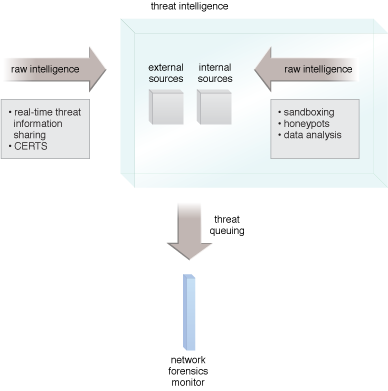
Figure 1 – A network forensics monitor queued by threat intelligence.
There are a number of standard threat-sharing frameworks available, including Structured Threat Information eXpression (STIX), Open Threat Exchange, Security Event System and Collective Intelligence Framework, among others.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


