Cloud Computing Patterns, Mechanisms > Data Management and Storage Device Patterns > Direct I/O Access
Direct I/O Access (Erl, Naserpour)
How can a virtual server overcome data transfer capacity thresholds imposed by its surrounding virtualization environment?

Problem
Virtualized networks and associated virtualized IT resources have capacity limitations that can unreasonably inhibit virtual server communication and data transfer performance.
Solution
The virtual server is allowed to circumvent the hypervisor and directly access the physical server’s I/O card.
Application
The hypervisor transfers complete control of the physical server’s I/O card directly to the virtual server, which is then able to recognize the I/O card as a hardware device.
Mechanisms
Cloud Storage Device, Cloud Usage Monitor, Hypervisor, Logical Network Perimeter, Pay-Per-Use Monitor, Resource Replication, Virtual Infrastructure Manager, Virtual Server
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
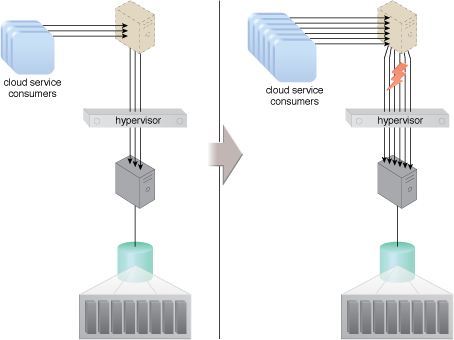
Part A (left) shows the virtual server accessing a database stored on a SAN storage LUN. Connectivity from the virtual server to the database occurs via a virtual switch. Part B (right) depicts an increase in the amount of requests. The resulting bandwidth and performance of the virtual NIC are inadequate.
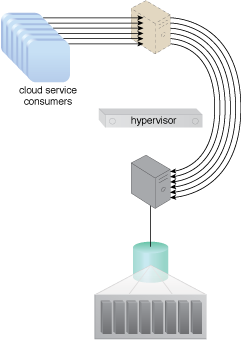
In Part C, the virtual server bypasses the hypervisor to connect to the database server via a direct physical link to the physical server. The increased workload can now be properly handled.
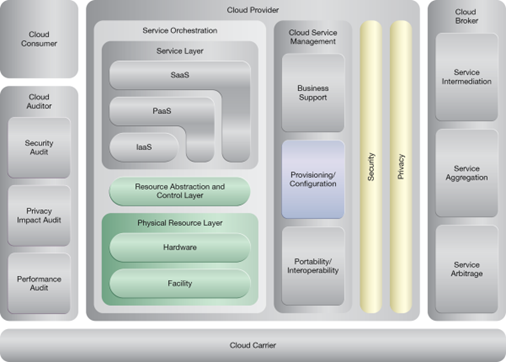
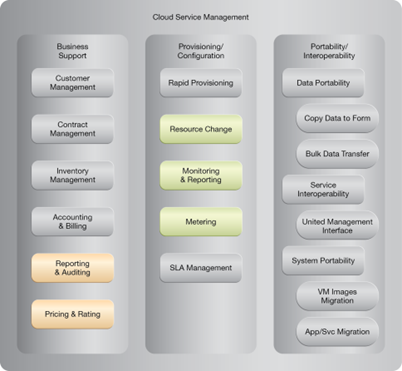
NIST Reference Architecture Mapping
This pattern relates to the highlighted parts of the NIST reference architecture, as follows:
This pattern is covered in CCP Module 5: Advanced Cloud Architecture.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This pattern is covered in CCP Module 14: Advanced Cloud Storage.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This pattern is covered in CCP Module 17: Advanced Cloud Virtualization.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is covered in:
Cloud Computing: Concepts, Technology & Architecture by Thomas Erl, Zaigham Mahmood,
Ricardo Puttini
(ISBN: 9780133387520, Hardcover, 260+ Illustrations, 528 pages)
For more information about this book, visit www.arcitura.com/books.



