Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Collaborative Monitoring and Logging
Collaborative Monitoring and Logging (R. Cope, S. Cope, Erl)
How can cloud monitoring and logging activities be coordinated between a cloud consumer and a cloud provider?

Problem
The cloud introduces a distributed compute platform that extends and distributes the organization’s computing boundaries and diminishes governance control. This introduces uncertainty in regards to whether it is the cloud consumer or cloud provider who is responsible for specific security monitoring and auditing tasks.
Solution
The organization determines security monitoring and auditing requirements, divides them between internal on-premise and external cloud providers, and establishes a security monitoring system that integrates both.
Application
Because of the distributed nature of security monitoring and the resulting collection of audit information, a process for sharing of audit information across parties is implemented. A coordinated implementation of Security Information and Event Management (SIEM) systems is accomplished or the cloud provider may provide attestations instead of direct monitoring capabilities to meet security monitoring and auditing requirements.
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
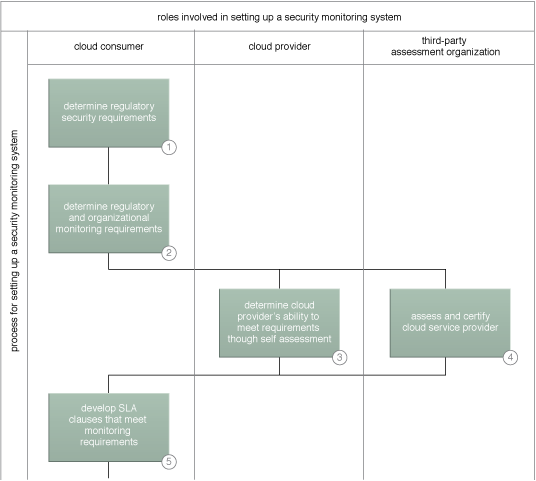
A sample process for selecting a cloud provider (Part I).
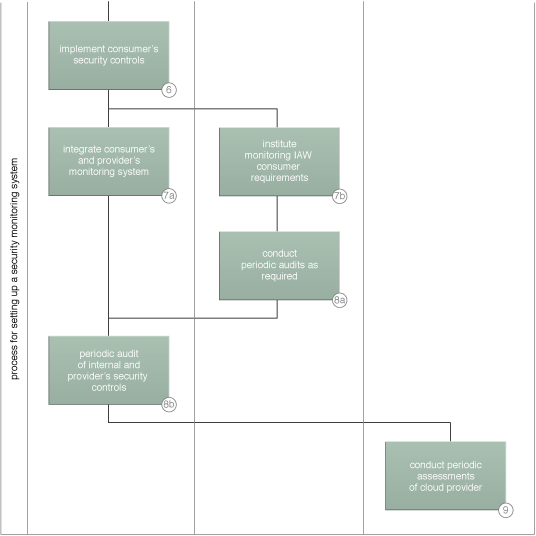
A sample process for selecting a cloud provider (Part II).
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


