Cloud Computing Patterns, Mechanisms > Mechanisms > I - P > Identity and Access Management
Identity and Access Management
The identity and access management (IAM) mechanism encompasses the components and policies necessary to control and track user identities and access privileges for IT resources, environments, and systems.
Specifically, IAM mechanisms exist as systems comprised of four main components:
- Authentication – Username and password combinations remain the most common forms of user authentication credentials managed by the IAM system, which can also support digital signatures, digital certificates, biometric hardware (fingerprint readers), specialized software (such as voice analysis programs), and locking user accounts to registered IP or MAC addresses.
- Authorization – The authorization component uses attribute services to define attributes and access control rules and oversees the relationships between identities, access control rights, and IT resource access.
- User Management – Related to the administrative capabilities of the system, the user management program is responsible for creating new user identities and access groups, resetting passwords, defining password policies, and managing privileges.
- Credential Management – The credential management system establishes and manages identities through credential issuance.
Although its objectives encompass the PKI mechanism, the IAM mechanism’s scope of implementation is larger because in addition to establishing identities, its structure encompasses access controls and policies in addition to assigning specific levels of user privileges. The IAM mechanism is primarily used to counter the insufficient authorization, denial of service, and overlapping trust boundary threats.
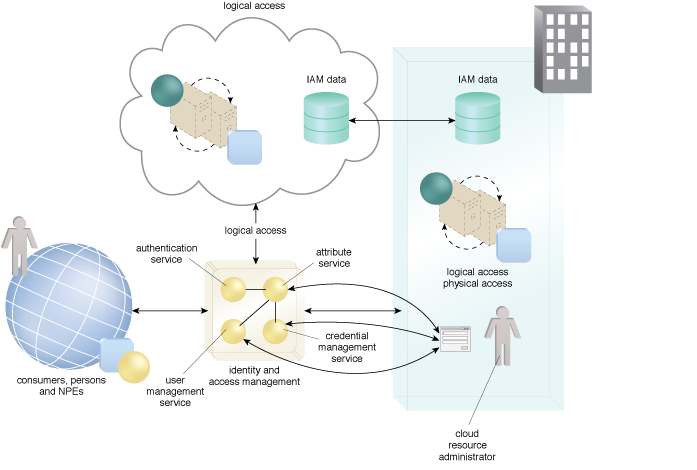
Figure 1 – An example of an IAM operational concept.
Figure 1 illustrates the main concepts for a robust IAM system, which include authentication of consumers and determination of authorization by referencing the consumer’s attributes, the resource’s attributes, and the environment. This requires that IAM data be managed, including consumer credential management and attribute management. The example in Figure 1 shows replication of IAM data between the cloud and on-premise databases, supporting access control decisions as well as for user and credential management. The authentication and authorization mechanisms should be located on the network for which they are being used to protect resources.
To achieve an advanced IAM architecture, IAM access control capabilities should be automated and data-driven to the greatest extent possible. This capability is known as dynamic access control and includes identification of consumers, their authentication and consideration of their attributes for an authorization or access decision. Access accountability capabilities include logging of consumer access to data, supported by the IAM which provides authentication and access information. The actual access control is carried out by the relying party and is not part of IAM.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


