Cloud Computing Patterns, Mechanisms > Sharing, Scaling and Elasticity Patterns > Broad Access
Broad Access (Erl, Naserpour)
How can cloud services be made accessible to a diverse range of cloud service consumers?

Problem
Cloud consumers may require access to a cloud service via cloud service consumer devices, protocols or data formats that the cloud service is not designed to support.
Solution
Runtime mapping logic is incorporated to transform data exchanges between the cloud service and different cloud service consumers.
Application
The mapping logic is added to the cloud service logic or positioned separately, within a multi-device broker mechanism that transforms data exchanged between the cloud service consumer and the cloud service.
Mechanisms
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
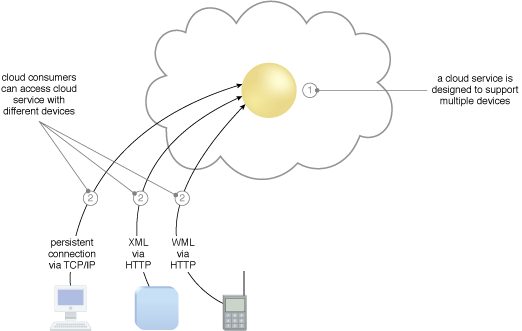
A cloud service containing runtime mapping logic is implemented (1) and made available to different kinds of cloud service consumer devices (2).

The cloud consumer (top) accesses and configures a physical server using a standard device and protocol that is now supported as a result of applying the Broad Access pattern. The cloud consumer (bottom) later accesses the cloud environment again to install a virtual server on the same physical server, and deploys an operating system and a database server. Both actions represent management tasks that can be accomplished via different devices brokered by the same centralized multi-device broker mechanism.
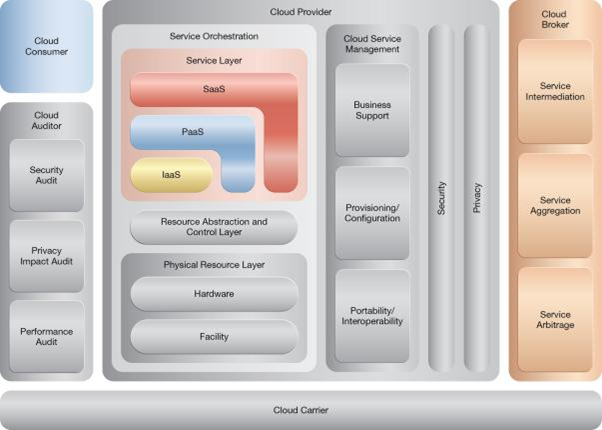
NIST Reference Architecture Mapping
This pattern relates to the highlighted parts of the NIST reference architecture, as follows:
This pattern is covered in CCP Module 4: Fundamental Cloud Architecture.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
