Cloud Computing Patterns, Mechanisms > Mechanisms > R - S > Security Information and Event Management System
Security Information and Event Management System

Security information and event management (SIEM) combines security information management (SIM) and security event management (SEM) functions into one security management system. SIEM collects relevant data about an enterprise’s security posture in multiple locations and analyzes all the data from a single point of view, providing the capability to spot trends and patterns that may be the result of malicious activity.
The SIEM system complements intrusion detection and prevention systems (IDPS) by correlating events logged by different technologies, displaying data from many event sources, and providing supporting information from other sources to help administrators verify the accuracy of alerts. SIEM data is usually recorded locally and sent to separate systems, such as centralized logging servers and the master SIEM system.
Advanced SIEM systems correlate event, threat, and risk information to detect attacks, possibly in realtime, and support forensic investigations and produce compliance reports as a result of activity monitoring.
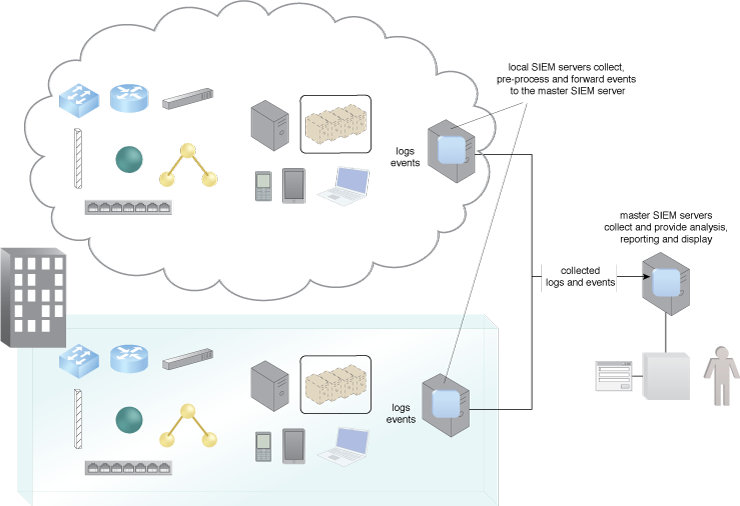
Figure 1 – An example of a SIEM architecture.
Figure 1 shows a SIEM architecture providing for log collection, analysis and forensics, event correlation, and IT compliance evidence for auditing and monitoring. Local SEM sensors located within the organization’s networks collect and forward events to a master SIEM.
Related Patterns:
- Collaborative Monitoring and Logging
- Independent Cloud Auditing
- Secure On-Premise Internet Access
- Threat Intelligence Processing
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


