Cloud Computing Patterns, Mechanisms > Reliability, Resiliency and Recovery Patterns > Resource Reservation
Resource Reservation (Erl, Naserpour)
How can shared IT resources be protected from conflicts that can arise from concurrent access?

Problem
When two or more cloud service consumers attempt to instantiate the same shared IT resource, runtime conflicts can occur, including resource constraints due to lack of capacity.
Solution
A system is established whereby a portion of an IT resource (or one or more IT resources) is set aside exclusively for a given cloud service consumer.
Application
The resource management system is used to define IT resource thresholds and to restrict access to reserved IT resources.
Mechanisms
Audit Monitor, Cloud Storage Device, Cloud Usage Monitor, Container, Hypervisor, Logical Network Perimeter, Remote Administration System, Resource Management System, Resource Replication, Virtual CPU, Virtual Infrastructure Manager, Virtual RAM, Virtual Server
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
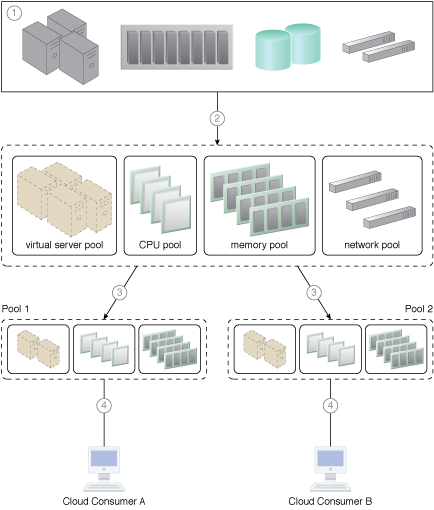
A resource pool hierarchy to which an IT resource reservation system is applied (Part I).
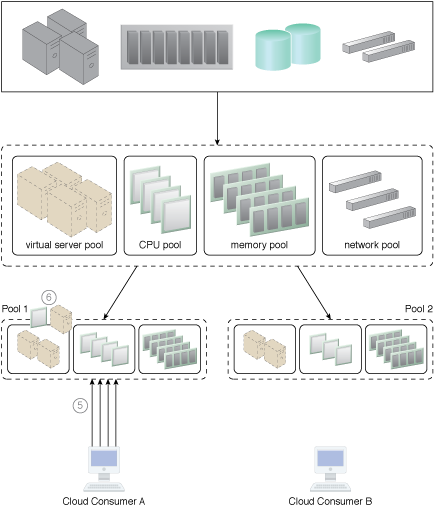
A resource pool hierarchy to which an IT resource reservation system is applied (Part II).
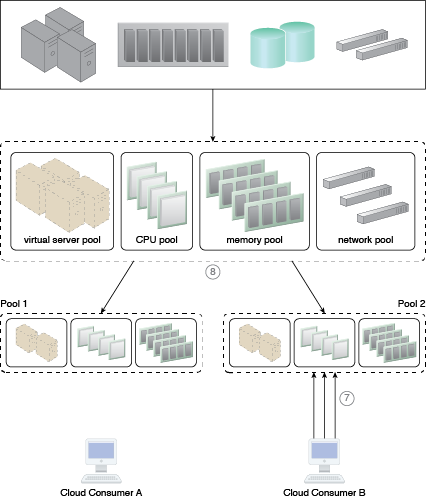
A resource pool hierarchy to which an IT resource reservation system is applied (Part III).
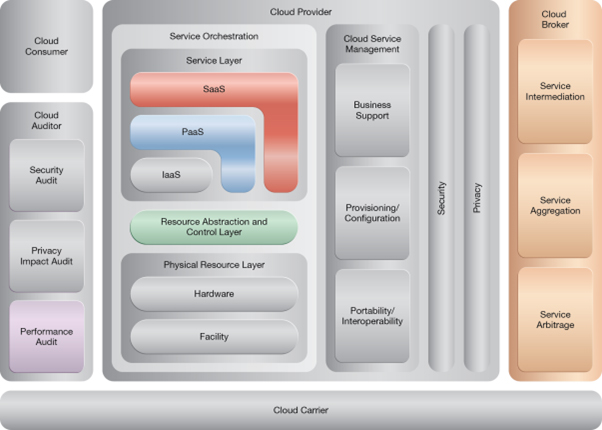
NIST Reference Architecture Mapping
This pattern relates to the highlighted parts of the NIST reference architecture, as follows:
This pattern is covered in CCP Module 4: Fundamental Cloud Architecture.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This pattern is covered in CCP Module 17: Advanced Cloud Virtualization.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is covered in:
Cloud Computing: Concepts, Technology & Architecture by Thomas Erl, Zaigham Mahmood,
Ricardo Puttini
(ISBN: 9780133387520, Hardcover, 260+ Illustrations, 528 pages)
For more information about this book, visit www.arcitura.com/books.


