Cloud Computing Patterns, Mechanisms > Basics > Multitenant Technology
Multitenant Technology
The multitenant application design was created to enable multiple users (tenants) to access the same application logic simultaneously. Each tenant has its own view of the application that it uses, administers, and customizes as a dedicated instance of the software while remaining unaware of other tenants that are using the same application.
Multitenant applications ensure that tenants do not have access to data and configuration information that is not their own. Tenants can individually customize features of the application, such as:
- User Interface – Tenants can define a specialized “look and feel” for their application interface.
- Business Process – Tenants can customize the rules, logic, and workflows of the business processes that are implemented in the application.
- Data Model – Tenants can extend the data schema of the application to include, exclude, or rename fields in the application data structures.
- Access Control – Tenants can independently control the access rights for users and groups.
Multitenant application architecture is often significantly more complex than that of single-tenant applications. Multitenant applications need to support the sharing of various artifacts by multiple users (including portals, data schemas, middleware, and databases), while maintaining security levels that segregate individual tenant operational environments.
Common characteristics of multitenant applications include:
- Usage Isolation – The usage behavior of one tenant does not affect the application availability and performance of other tenants.
- Data Security – Tenants cannot access data that belongs to other tenants.
- Recovery – Backup and restore procedures are separately executed for the data of each tenant.
- Application Upgrade – Tenants are not negatively affected by the synchronous upgrading of shared software artifacts.
- Scalability – The application can scale to accommodate increases in usage by existing tenants and/or increases in the number of tenants.
- Metered Usage – Tenants are charged only for the application processing and features that are actually consumed.
- Data Tier Isolation – Tenants can have individual databases, tables, and/or schemas isolated from other tenants. Alternatively, databases, tables, and/or schemas can be designed to be intentionally shared by tenants.
A multitenant application that is being concurrently used by two different tenants is illustrated in Figure 5.11. This type of application is typical with SaaS implementations.
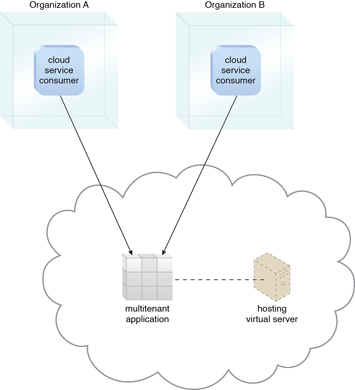
Figure 1 – A multitenant application that is serving multiple cloud service consumers simultaneously.
Multitenancy vs. Virtualization
Multitenancy is sometimes mistaken for virtualization because the concept of multiple tenants is similar to the concept of virtualized instances.
The differences lie in what is multiplied within a physical server acting as a host:
- With virtualization: Multiple virtual copies of the server environment can be hosted by a single physical server. Each copy can be provided to different users, can be configured independently, and can contain its own operating systems and applications.
- With multitenancy: A physical or virtual server hosting an application is designed to allow usage by multiple different users. Each user feels as though they have exclusive usage of the application.
