Cloud Computing Patterns, Mechanisms > Mechanisms > T - Z > Threat Intelligence System
Threat Intelligence System

Threat intelligence is evidence-based knowledge, including context, indicators, implications, and actionable advice, that can provide information about an existing or emerging threat to an asset that can be used to inform decisions as to how the organization should respond to that threat. Common forms of threat intelligence data include security threats, threat actors, exploits, malware, vulnerabilities, and compromise indicators.
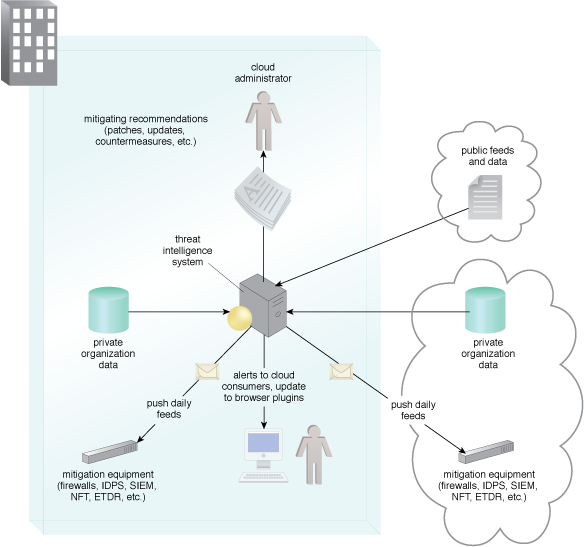
Figure 1 – A threat intelligence system architecture.
Figure 1 shows collection, analysis, distribution and use of analysis information in a threat intelligence system. The data is automatically distributed to attack mitigation components in the enterprise, providing automatic updates of security configurations. The automatic updates can extend to cloud consumers’ browser protection systems.
Attackers commonly attempt to take advantage of web browsers and their vulnerabilities. Threat intelligence can provide whitelists and blacklists of safe and compromised websites that can alert for new vulnerabilities and when security patches are available.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


