Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Threat Intelligence Processing
Threat Intelligence Processing (Cope, Erl)
How can actionable threat indicators be generated to detect threats and prevent cloud vulnerability exploits?

Problem
Organizations are not normally able to take advantage of the large volume of available threat data that can provide indications of the kind of attacks to expect and where they can originate. This can result in missed opportunities to detect hidden security vulnerabilities and prevent them from being exploited.
Solution
Incorporating a threat intelligence system into the cloud security architecture allows organizations to forecast attacks, alert administrators and cloud consumers, and utilize the intelligence to prevent and defend against future attacks.
Application
A threat intelligence system is implemented to receive and process external intelligence feeds, as well as intelligence gained from analyzing attacks internally, to automatically queue security systems such as security information and event management systems (SIEMs), network forensics monitor (NFM), endpoint threat detection and response systems (ETDRs) and intrusion detection and protections systems (IDPSs), and also to alert cloud administrators and consumers.
Mechanisms
Endpoint Threat Detection and Response, Honeypot, Intrusion Detection and Prevention Systems, Malware Hash, Network Forensic Monitor, Sandbox, Security Information and Event Management System, Threat Intelligence System
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
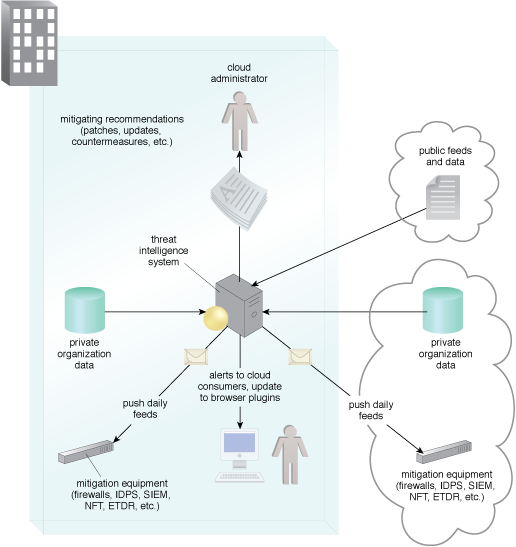
An example of a typical threat intelligence analysis architecture.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


