Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Secure On-Premise Internet Access
Secure On-Premise Internet Access (Cope, Erl, Kristan)
How can a network segment with Internet access be secured?

Problem
The security profile for a network segment that has Internet access is equivalent to that of the Internet, which makes assets, internal or cloud, vulnerable to attacks over this segment.
Solution
A system can be established whereby an Internet access segment consisting of network elements that support outbound interactions from the site to external entities via the Internet and all inbound interactions are handled via a controlled sharing (DMZ) segment. This DMZ segment contains mitigations to the current attacks and connection to cloud resources is established from a separate trusted network segment using cryptography.
Application
Using firewall and router security mechanisms, subnets with access controls lay the foundation for separating and protecting resources and at the same time provide required Internet access.
Mechanisms
Application Delivery Controller, Domain Name Service, Intrusion Detection and Prevention Systems, Security Information and Event Management System, Virtual Private Network
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
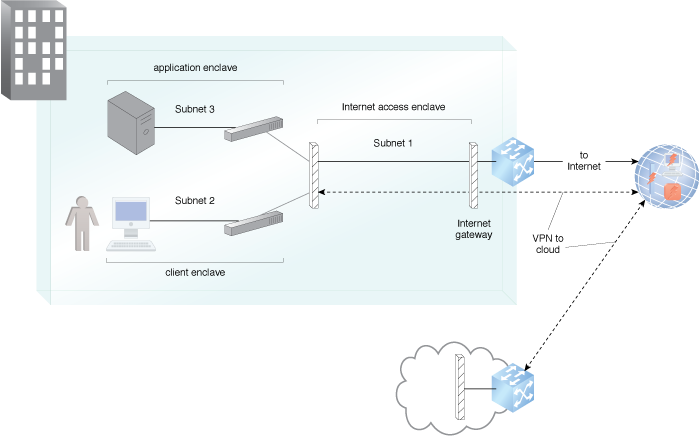
An example of subnet segmentation, firewalls and NAT provider protection from Internet intruders.
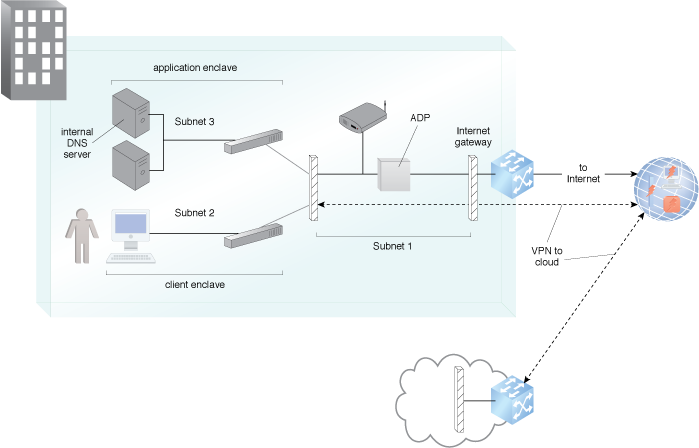
An example of the application of the Secure Internet Access pattern.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


