Cloud Computing Patterns, Mechanisms > Mechanisms > T - Z > Traffic Filter
Traffic Filter
Traffic filtering is a method used to provide network security by filtering network traffic based on many types of criteria. Traffic filters are used as distributed denial-of-service (DDoS) protection devices that provide ingress filtering, rate limiting, reverse address lookup, and network traffic monitoring. Inbound filters are employed by routers to limit traffic towards a network to authorized traffic only, and to specify rules and policies that govern a specific port, service, server or network. Inbound filters are implemented in network hardening and security planning to manage the traffic flow and allow only secure and trusted networks, hosts or autonomous systems to access the protected network.
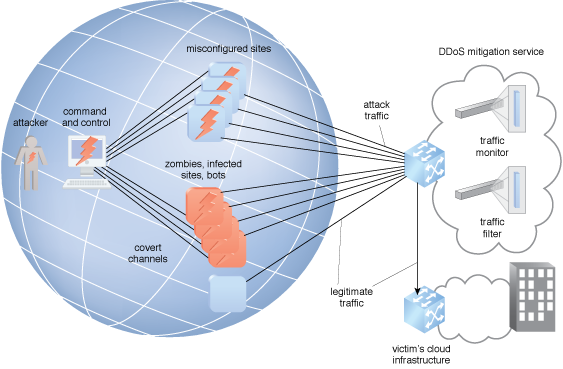
Figure 1 – An example of a DDoS mitigation service using a traffic filter.
Figure 1 illustrates the use of a DDoS mitigation service using a traffic filter. Botnet traffic filtering (BTF) uses cloud technology to identify and block potential botnet traffic. BTF detects transit connections to and from known malware and botnet control sites. When internal resources are infected with malware and attempt to contact the command and control server across the network, the BTF also alerts the system administrator. The BTF can be informed by the threat intelligence system by receiving a blacklist of malicious domain names. BTF uses dynamic filter DNS snooping to look at User Datagram Protocol (UDP) DNS replies, and builds a DNS reverse cache that maps the IP addresses in those replies to the domain names they match as a tool to detect attacking domains.
Because the hosts and controllers in a botnet are operating from captured resources, botnets are dynamic and short-lived. As soon as one botnet is closed down, it will show up in a different place with new addresses, operating like a network version of a morphing virus.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


