Cloud Computing Patterns, Mechanisms > Mechanisms > R - S > Secure Token Service
Secure Token Service

A secure token service (STS) issues security tokens as a result of consumer requests for single sign-on (SSO) tokens. The STS authenticates the consumer and issues a security token that contains consumer claims and is protected from manipulation by a digital signature. Example tokens issued include Kerberos and SAML.
The STS provides:
- Enforcement of organizational identification and authentication policies and requirements.
- Production of a standardized security token for relying parties to consume for access control decisions.
- Interface with authoritative data sources to verify claims and produce accurate security assertions.
- Security controls to provide a set of countermeasures against security threats.
- Centralized identification and authentication services to offload redundant security requirements from relying parties. It is extensible to support various security token requirements.
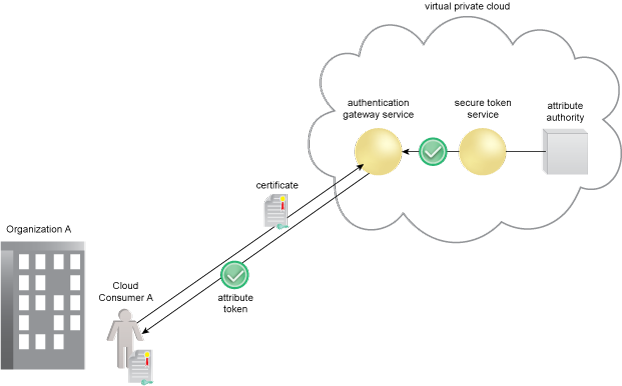
Figure 1 – An example of an STS providing attribute tokens to an authentication gateway service.
Figure 1 assumes that the STS has been provisioned with Organization A’s cloud consumer attributes. Organization A has developed Service A and Service B to use the tokens passed on by the authentication gateway service (AGS), which uses the attributes issued by the STS to make access control decisions. The consumer authenticates to the AGS which requests an attribute token from the STS. The AGS supplies the attribute token to the consumer for presenting their authentication status and attributes to relying party cloud services.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


