Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Cloud Authentication Gateway
Cloud Authentication Gateway (Cope, Erl, Ahmed)
How can cloud-based IT resources be made accessible to cloud service consumers with diverse protocol requirements?

Problem
Cloud consumers are compelled to support multiple authentication, communication and session protocols when cloud service providers deliver components, applications, and service compositions with diverse protocol requirements.
Solution
An authentication service is implemented, allowing standard authentication, communication, and session establishment from a cloud consumer to the authentication service. The authentication service then authenticates to the cloud resource on behalf of the cloud consumer using the diverse protocols required by the cloud provider.
Application
An authentication gateway service (AGS) is established as a reverse proxy front end between the cloud consumer and the cloud resource, which intercepts and terminates the consumer’s encrypted network connection, authenticates the cloud consumer, authenticates itself and the consumer to the cloud provider, and then proxies all communication between the two. All three parties are authenticated in some combination of transport level or application level communication.
Mechanisms
Authentication Gateway Service, Certificate, Certificate Authority, Certificate Revocation List, Public Key Infrastructure, Secure Token Service, Virtual Private Network
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
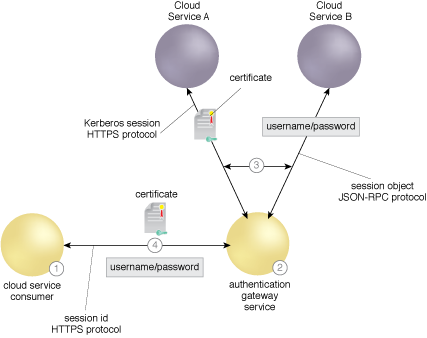
A consumer only needs to support a single set of standard protocols using the AGS.
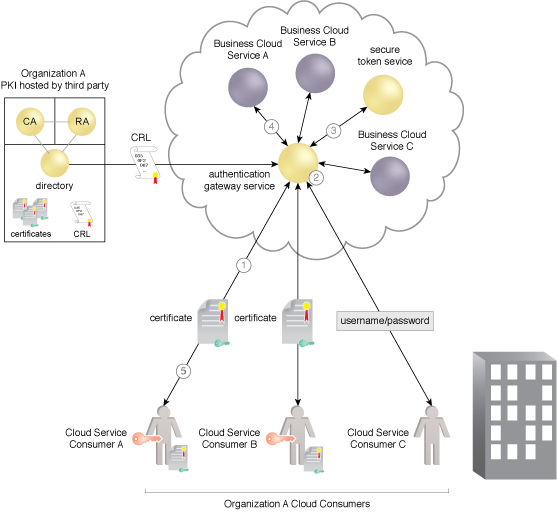
The AGS as a reverse proxy brokering among multiple authentication, communication, and session protocols.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


