Cloud Computing Patterns, Mechanisms > Mechanisms > T - Z > Traffic Monitor
Traffic Monitor

Network traffic monitoring is the process of reviewing, analyzing and managing network traffic for any abnormality or process that can affect network performance, availability and/or security. The traffic monitor allows categorization of a network’s bandwidth usage to provide information about the characteristics of an attack for execution of mitigation techniques by a traffic filter.
Traffic filters provide network, transport, and application layer protocol analysis to detect DDoS attacks. Traffic filtering is commonly provided by host-based firewalls to prevent the attack and route traffic to a DDoS mitigation service when an attack is detected. Figure 1 shows the traffic monitor detection of a traffic hijack attack. Traffic monitors need to communicate with traffic filters to detect multi-dimensional attacks. Attacks can be hijack or DDoS volume-based, protocol-based, or application layer-based, and can be network layer, transport layer, or application layer oriented. Often, attacks are multi-dimensional in terms of type and layer of attack.
Traffic monitors need to queue the traffic filter to ongoing attacks, including integration with threat intelligence systems, to be aware of the constantly changing botnet landscape. Netflow monitoring is a standard monitoring tool and method that allows for determination of the ingress point of spoofed DoS/DDoS attacks. Detailed network characteristics can be determined to execute mitigations to block only the attack, with minimal impact on legitimate traffic.
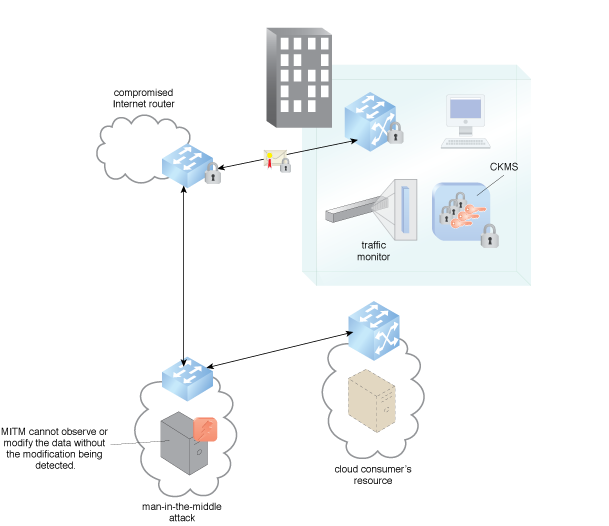
Figure 1 – An example of a traffic monitor monitoring for a hijack of network traffic.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


