Cloud Computing Patterns, Mechanisms > Mechanisms > I - P > Intrusion Detection and Prevention Systems
Intrusion Detection and Prevention Systems

Intrusion detection and prevention systems (IDPS) automate the process of monitoring events that occur in a computer system or network, and attempt to identify possible incidents, log information about them, stop them, and report them to security administrators. They are typically used to record information related to observed events, notify security administrators of important observed events, and automatically generate reports with some remediation actions performed manually after human review of the reports. Many IDPSs can also be configured to respond to a detected threat using a variety of techniques, including changing security configurations or blocking the attack.
For pre-infection threat prevention, IDPS blocks exploitation of known application vulnerabilities. Their anti-malware functions block exploitation of data-driven application vulnerabilities. The IDPS enforces protocols and data compliance. Post-infection threat prevention detects and blocks interactions with bot command and control servers. IDPS controls block leakage of sensitive data to destinations outside of the organization.
Figure 1 shows an IDPS located at a network node protecting multiple subnets.
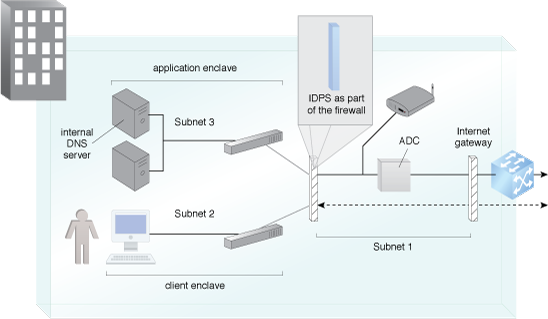
Figure 1 – An example of an IDPS as part of a firewall.
Related Patterns:
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


