Cloud Computing Patterns, Mechanisms > Mechanisms > T - Z > Trusted Platform Module
Trusted Platform Module

A trusted platform module (TPM) is a tamper-resistant integrated circuit built into some computer motherboards that can perform cryptographic operations, such as key generation, and protect small amounts of sensitive information, such as passwords, measurement data for boot software and cryptographic keys. The TPM is used to store platform measurements that help ensure that the platform remains trustworthy. Authentication and attestation are necessary steps to attain trust to a policy-specified level of security assurance.
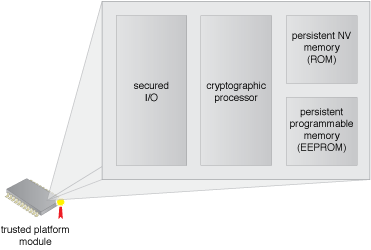
Figure 1 – An example of a trusted platform module as part of the resource’s hardware.
The compute platform must have a root of trust for measurement (RTM) that is implicitly trusted to provide an accurate validation of the boot code modules. The TPM provides root of trust for reporting and a root of trust storage for the RTMs. The TPM contains a set of registers that contain RTM measurements for launch modules of the boot software. The TPM uses an attestation identity key to sign messages to an attestation service, which must validate the signature and the register contents.
The TPM stores a set of “known good” measurements of boot components that are securely generated and stored. The attestation service stores the results of the platform trusted boot reported by the TPM. Maintenance of the known good measurements for different hypervisors, operating systems and various BIOS software and ensuring they are protected from tampering and spoofing is critical. For instance, based on security requirements, remote BIOS flashing should be disabled and separation of duties (SOD) by multiple administrators should be employed to establish a reasonable level of security assurance.
Related Patterns:
- Cloud Storage Data Placement Compliance Check
- Geotagging
- Hypervisor Protection
- Trust Attestation Service
- Trusted Cloud Resource Pools
- Trusted Platform BIOS
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


