Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > In-Transit Cloud Data Encryption
In-Transit Cloud Data Encryption (Cope, Erl)
How can data be securely transmitted to, from, and within a cloud environment?

Problem
Data copied to and from a cloud environment transits networks and servers beyond the control of the organization and can be intercepted by malicious intermediaries.
Solution
A solution is implemented with capabilities that secure and protect data while it transfers between sender and receiver and also ensure that data will not be accepted by the receiver if the original data sent is modified.
Application
An encryption mechanism is implemented to encrypt data between sender and receiver for confidentiality, and a digital signature mechanism is implemented to provide integrity for the data.
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
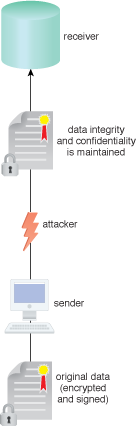
An attacker attempts to intercept data uploading into a cloud environment, however, the data is encrypted and signed before it is sent.
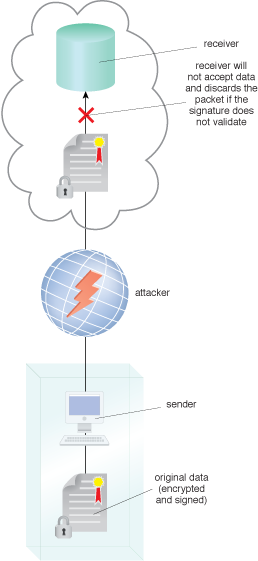
An attacker intercepts encrypted data before it is received by the cloud provider, and the receiver discards the packet as a result of maintaining data integrity and confidentiality.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


