SOA Patterns > Service Interaction Security Patterns > Direct Authentication
Direct Authentication (Hogg, Smith, Chong, Hollander, Kozaczynski, Brader, Delgado, Taylor, Wall, Slater, Imran, Cibraro, Cunningham)
How can a service verify the credentials provided by a consumer?

Problem
Some of the capabilities offered by a service may be intended for specific groups of consumers or may involve the transmission of sensitive data. Attackers that access this data could use it to compromise the service or the IT enterprise itself.
Solution
Service capabilities require that consumers provide credentials that can be authenticated against an identity store.
Application
The service implementation is provided access to an identity store, allowing it to authenticate the consumer directly.
Impacts
Consumers must provide credentials compatible with the service’s authentication logic. This pattern may lead to multiple identity stores, resulting in extra governance burden.
Principles
Architecture
Composition, Service
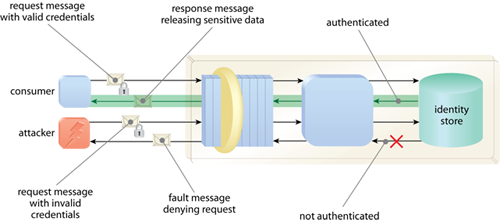
By having the service authenticate consumer requests against an identity store, only safe consumers can access sensitive data and logic.
Related Patterns in This Catalog
Brokered Authentication, Data Confidentiality, Data Origin Authentication, Service Perimeter Guard, Trusted Subsystem
Related Service-Oriented Computing Goals
This pattern is covered in SOACP Module 18: Fundamental Security for Services, Microservices & SOA.
For more information regarding the SOA Certified Pofessional (SOACP) curriculum,
visit www.arcitura.com/soa.
This page contains excerpts from:
SOA Design Patterns by Thomas Erl
(ISBN: 0136135161, Hardcover, Full-Color, 400+ Illustrations, 865 pages)
For more information about this book, visit www.arcitura.com/books.

