SOA Patterns > Service Security Patterns > Service Perimeter Guard
Service Perimeter Guard (Hogg, Smith, Chong, Hollander, Kozaczynski, Brader, Delgado, Taylor, Wall, Slater, Imran, Cibraro, Cunningham)
How can services that run in a private network be made available to external consumers without exposing internal resources?

Problem
External consumers that require access to one or more services in a private network can attack the service or use it to gain access to internal resources.
Solution
An intermediate service is established at the perimeter of the private network as a secure contact point for any external consumers that need to interact with internal services.
Application
The service is deployed in a perimeter network and is designed to work with existing firewall technologies so as to establish a secure bridging mechanism between external and internal networks.
Impacts
A perimeter service adds complexity and performance overhead as it establishes an intermediary processing layer for all external to internal communication.
Principles
Architecture
Service
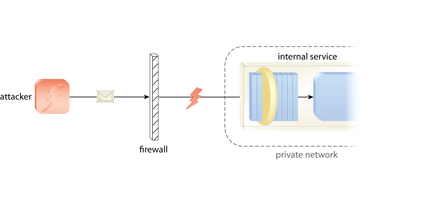
The perimeter service processes the attacker’s message and upon determining its malicious intent, rejects it. This spares the underlying internal service from exposure and unnecessary security-related processing.
Related Patterns in This Catalog
Brokered Authentication, Direct Authentication, Exception Shielding, Inventory Endpoint, Message Screening, Utility Abstraction
Related Service-Oriented Computing Goals
This pattern is covered in SOACP Module 19: Advanced Security for Services, Microservices & SOA.
For more information regarding the SOA Certified Pofessional (SOACP) curriculum,
visit www.arcitura.com/soa.
This page contains excerpts from:
SOA Design Patterns by Thomas Erl
(ISBN: 0136135161, Hardcover, Full-Color, 400+ Illustrations, 865 pages)
For more information about this book, visit www.arcitura.com/books.

