Cloud Computing Patterns, Mechanisms > Network Security, Identity & Access Management and Trust Assurance Patterns > Federated Cloud Authentication
Federated Cloud Authentication (Cope, Erl)
How can X.509 certificates from a federation of cloud consumers be authenticated when an associated certificate revocation list fails?

Problem
If the certificate revocation list (CRL) corresponding to a cloud consumer’s certificate is unavailable, either from communication or public key infrastructure (PKI) failure, cloud service providers are unable to authenticate submitted certificate credentials.
Solution
Federated authentication allows cloud services to authenticate cloud consumers incorporating a certificate status checking responder on the local area network (LAN), which supports authentication independently when the CRL for a given organization is unavailable due to failure.
Application
A local certificate validation service (CVS) is implemented to check the revocation status of submitted certificates from multiple organizations.
Mechanisms
Certificate, Certificate Authority, Certificate Revocation List, Certificate Validation Service, Public Key Infrastructure
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
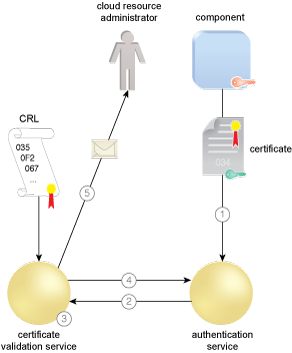
The component as a cloud service consumer sends the required certificate to an authentication service to be authenticated (1). The authentication service sends a request to the CVS that includes the issuer and serial number of the certificate (2). The CVS compares the serial number with the associated issuer’s CRL to determine if the certificate is revoked (3). The CVS signs a response indicating if the certificate is good, revoked, or unknown (4). The CVS also checks to see if the CRL is valid. If the CRL is stale and the CVS cannot retrieve a current one, the CVS can be configured to send an alert to a cloud resource administrator (5).
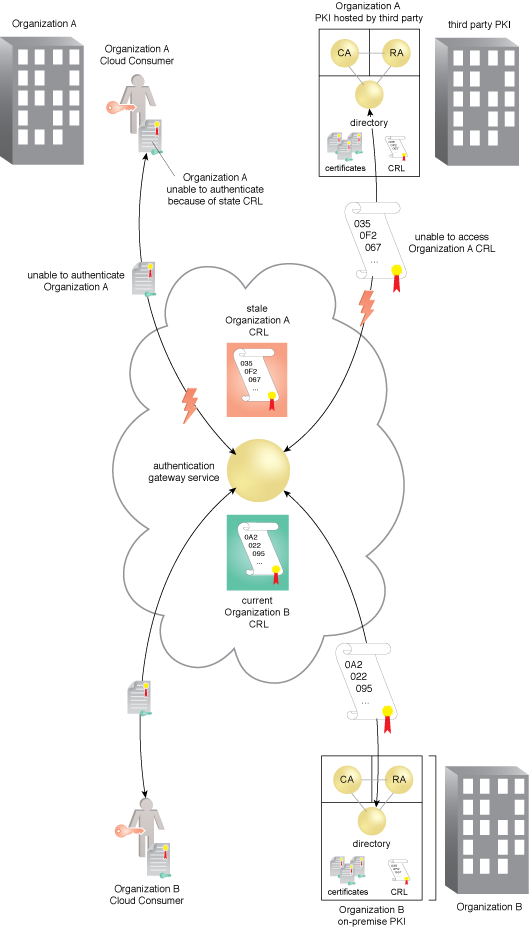
With the implementation of a CVS, the availability problems associated with an expired CRL are mitigated.
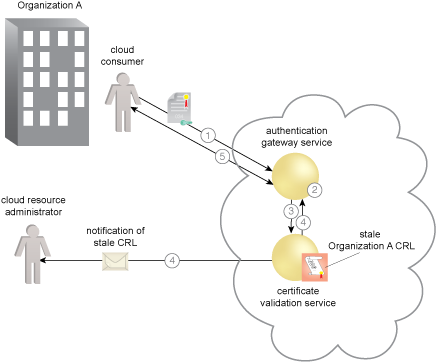
Resilient certificate validation in a cloud.
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


