Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Permanent Data Loss Protection
Permanent Data Loss Protection (Cope, Erl)
How can cloud consumers protect themselves from permanently losing their data?

Problem
Data can be permanently lost due to malicious attackers or from deletion by a cloud service provider, either through negligence or disaster. If encryption is being used on data and the encryption key is lost, the data is also lost.
Solution
A data retention policy is created and implemented as part of a security policy to mandate that backups of data and keys are created and maintained.
Application
Data is inventoried and assigned a sensitivity factor and a risk of loss factor, is encrypted and backed up in a location separate from the primary infrastructure, and the cloud consumer verifies that the cloud provider meets the data retention policy. A cryptographic key management system (CKMS) is implemented under the direct control of the data owner and is also backed up.
Mechanisms
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
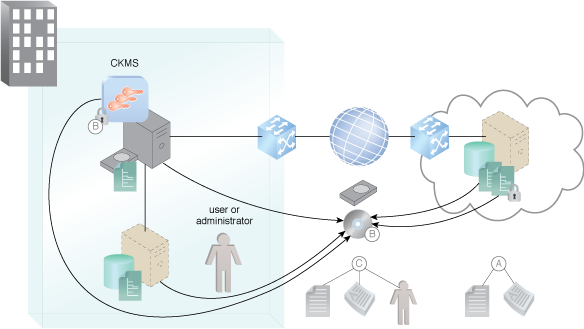
Data retention policy, which normally meets a compliance requirement, requires an inventory of all sensitive data, the sensitivity level of the data, the risk of loss and backup schedules and forms (A). Backups of data and encryption keys are created according to policy, and backup copies are stored off-site and separate from the operational data so that risks of loss are mitigated (B). Periodic audits ensure compliance with policy (C).
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


