Cloud Computing Patterns, Mechanisms > Cloud Service and Storage Security Patterns > Mobile BYOD Security
Mobile BYOD Security (Cope, Erl)
How can mobile device access to IT resources be secured?

Problem
Consumers often need to access enterprise information systems, whether they are on-premise or remote, using mobile devices including laptops, tablets, and smart phones, which pose special security requirements.
Solution
According to the BYOD security requirements and policy developed, a security framework is established to monitor, control and protect the mobile devices, their applications and data, and their network connections.
Application
An enterprise mobility management (EMM) system is implemented, covering the special security requirements of mobile devices.
Mechanisms
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
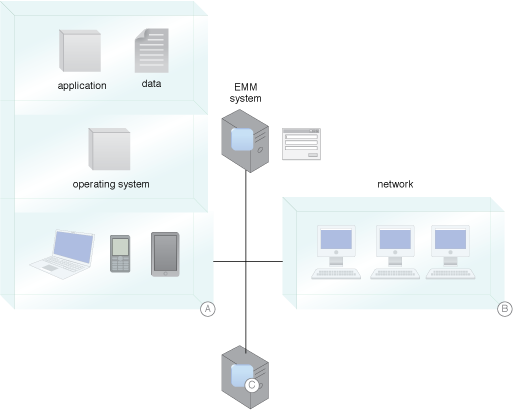
Solutions for monitoring, controlling, and protecting mobile devices include the device (A), network (B), and integrating with corporate SIEM and logging systems for visibility and monitoring for compliance (C).
This mechanism is covered in CCP Module 7: Fundamental Cloud Security and
in Module 8: Advanced Cloud Security.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
The architectural model upon which this design pattern is based is further covered in:
Cloud Computing Design Patterns by Thomas Erl, Robert Cope, Amin Naserpour
(ISBN: 9780133858563, Hardcover, ~ 528 pages)
For more information about this book, visit www.arcitura.com/books.


