Big Data Patterns, Mechanisms > Data Maintenance Patterns > Centralized Access Management
Centralized Access Management (Buhler, Erl, Khattak)
How can access to resources within a Big Data platform be managed efficiently and consistently?

Problem
Solution
Application
Mechanisms
A security engine is used to enable security policy authoring via a graphical user interface. Generally, a set of policies are created by the system administrator for each resource. Depending on the nature of the resource, the policy contains different levels of granularity. For example, in the case of a distributed file system, the policy includes permissions at the directory level. However, in the case of a NoSQL database, the policy normally includes permissions for table and individual columns. Permissions are configured by adding user IDs or user groups and granting access as required.
Internally, a plugin exists for each resource that acts as an intermediary by handling resource access requests. The plugin consults the relevant security policy and performs authorization based on the permissions set in the policy. Some security engines may also provide access auditing features in the form of a log file.
In order to ensure longevity of the security engine in the face of Big Data platform evolution (addition of new resources), its extensibility needs to be taken into account to evaluate how easy would it be to integrate new resources. In case a plugin is not available for a particular resource, in-hose development of the plugin may be required.
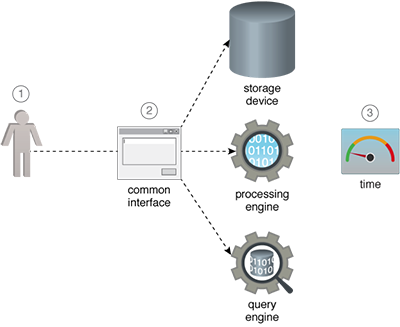
Functionality is added to the Big Data platform that enables specifying polices for different resources within the Big Data platform via a central interface. When a user accesses a resource, such as the distributed file system, the corresponding policy defined for that resource is checked, and access is granted or denied based on the permissions set in the policy.
- A system administrator needs to configure security for different components in a Big Data platform.
- The system administrator secures each component individually through a centralized interface.
- The entire configuration process takes a short time to complete.
This pattern is covered in BDSCP Module 11: Advanced Big Data Architecture.
For more information regarding the Big Data Science Certified Professional (BDSCP) curriculum,
visit www.arcitura.com/bdscp.
The official textbook for the BDSCP curriculum is:
Big Data Fundamentals: Concepts, Drivers & Techniques
by Paul Buhler, PhD, Thomas Erl, Wajid Khattak
(ISBN: 9780134291079, Paperback, 218 pages)
Please note that this textbook covers fundamental topics only and does not cover design patterns.
For more information about this book, visit www.arcitura.com/books.

