Cloud Computing Patterns, Mechanisms > Mechanisms > I - P > Logical Network Perimeter
Logical Network Perimeter

The logical network perimeter establishes a virtual network boundary that can encompass and isolate a group of related cloud-based IT resources that may be physically distributed. It is defined as the isolation of a network environment from the rest of a communications network.
The logical network perimeter can be implemented to:
- isolate IT resources in a cloud from non-authorized users
- isolate IT resources in a cloud from non-users
- isolate IT resourced in a cloud from cloud consumers
- control the bandwidth that is available to isolated IT resources
Logical network perimeters are typically established via network devices that supply and control the connectivity of a data center and are commonly deployed as virtualized IT environments that include:
- Virtual Firewall – An IT resource that actively filters network traffic to and from the isolated network while controlling its interactions with the Internet.
- Virtual Network – Usually acquired through VLANs, this IT resource isolates the network environment within the data center infrastructure.

Figure 1 – The symbols used to represent a virtual firewall (left) and a virtual network (right).
Figure 1 introduces the notation used to denote these two IT resources. Figure 2 depicts a scenario in which one logical network perimeter contains a cloud consumer’s on-premise environment, while another contains a cloud provider’s cloud-based environment. These perimeters are connected through a VPN that protects communications, since the VPN is typically implemented by point-to-point encryption of the data packets sent between the communicating endpoints.
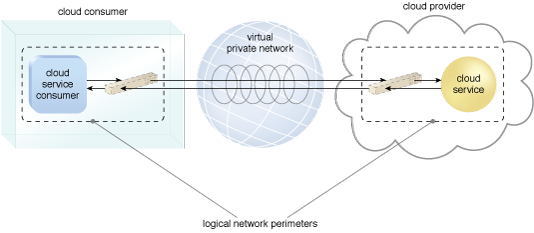
Figure 2 – Two logical network perimeters surround the cloud consumer and cloud provider environments.
Related Patterns:
- Bare-Metal Provisioning
- Centralized Remote Administration
- Direct I/O Access
- Elastic Network Capacity
- Hypervisor Clustering
- Load Balanced Virtual Server Instances
- Load Balanced Virtual Switches
- Logical Pod Container
- Multipath Resource Access
- Persistent Virtual Network Configuration
- Redundant Physical Connection for Virtual Servers
- Resource Management
- Resource Pooling
- Resource Reservation
- Self-Provisioning
- Shared Resources
- Single Node Multi-Containers
- Storage Workload Management
- Workload Distribution
- Zero Downtime
This mechanism is covered in CCP Module 4: Fundamental Cloud Architecture.
For more information regarding the Cloud Certified Professional (CCP) curriculum, visit www.arcitura.com/ccp.
This cloud computing mechanism is covered in:
Cloud Computing: Concepts, Technology & Architecture by Thomas Erl, Zaigham Mahmood,
Ricardo Puttini
(ISBN: 9780133387520, Hardcover, 260+ Illustrations, 528 pages)
For more information about this book, visit www.arcitura.com/books.

